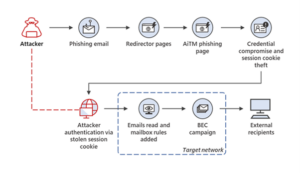
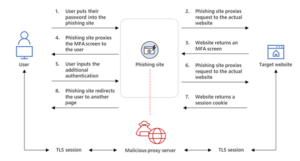
How can I protect my organisation against AiTM attacks?
While there are specific items that will stop this type of attack dead in its tracks, security requires a multi-layered or defense in depth approach. While you could scroll down to the prevention section, and immediately implement those preventions, you will still be leaving your organisation open to other potentially unknown, or uncommon threats.
This attack showcases how security is an ever-evolving landscape – blue teams and red teams are constantly trying to one-up each other, and always will be. Security is a journey, not a destination.
To stay ahead of evolving threats, your organisation must implement prevention measures (and regularly review these), as well as having ongoing detection and response capabilities to detect any active threats or successful breaches.
Detect and Respond
Detect
Microsoft security products offer numerous advanced detection and response capabilities – this is one reason why we have built our Managed Detection & response (MDR) services on these technologies.
Microsoft recently announced that automatic attack disruption capability for AiTM attacks had become generally available. This automatic response will trigger based on a high-confidence identification of an AiTM attack, from multiple correlated Microsoft 365 Defender signals.
In addition to the above automatic disruption capability, additional alerting should be leveraged.
Microsoft Defender for Endpoint will raise an alert when it detects a user accessing a potential phishing website.
Microsoft 365 Defender will alert when a stolen cookie was used.
Microsoft Defender for Office 365 will alert upon the creation of a forwarding/redirection inbox rule. In addition, we recommend reviewing the age of a domain that’s used within an attack. Approximately 70% of newly registered domains are found to be malicious.
Microsoft Defender for Cloud Apps detects AiTM phishing and business email compromise (BEC) attacks by using the following alerts:
- Suspicious inbox manipulation rule. As part of an AiTM/BEC attack, attackers set inbox rules to hide their activities. This action is not normally performed by users, and is therefore suspicious behaviour. This alert will notify security teams when this happens for investigation.
- Impossible travel activity alert. If your users normally sign-in from the UK at 9AM, but then one of your users also signs-in from New York, an hour later – that’s impossible. It is not possible to travel to that location within that time and could indicate the user is compromised, and their account is being used elsewhere.
- Activity from infrequent country alert. Attackers may use VPNs or proxies to hide their true location however the egress location of these services might be uncommon based on the user’s previously monitored sign-in logs, raising an alert for investigation.
Entra ID Identity Protection automatically detects identity-based risks and suspicious sign-in attempts, and raises any of these alerts:
- Anomalous Token use. This alert will fire when a token is used with unusual characteristics, such as being used from an unfamiliar location.
- Unfamiliar sign-in properties. This alert will fire when a sign-in occurs with properties such as device and location that do not match previously observed sign-in properties for the user.
- Anonymous IP address. This alert will flag any sign-in attempts from anonymising services, such as an anonymous VPN service or the Tor browser.
Respond
Responses will vary depending on the severity of the attack, but as a general rule of thumb, you should perform the following actions to remediate the compromised identity:
- Revoke session cookies and reset password.
- Review and revoke MFA setting changes made by the attacker on the compromised user. For example, remove any unknown or unexpected MFA methods.
Your organisations CSOC should monitor and respond to these alerts as soon as possible.
Prevent
Detection and Response is a key component of responding to threats in real time, however once a threat and its prevention methods are identified, they should be implemented as soon as possible.
There are three main areas to look at when preventing this type of attack. The first is understanding MFA methods, and the protections that offer. The second area is phish-resistant MFA methods. The third is Entra ID Conditional Access controls, and the protections offered.
MFA Methods
No standard MFA method will protect against AiTM.
| Method |
Provides protection for AiTM? |
| SMS |
No |
| Phone call / voice call |
No |
| Microsoft Authenticator app (push notification) |
No |
| Microsoft Authenticator app and number matching |
No |
| Microsoft Authenticator app and additional context |
No |
| Microsoft Authenticator app, additional context and number matching |
No |
Phish-resistant MFA methods
Hardware-backed MFA methods will provide protection against AiTM.
| Method |
Provides protection for AiTM? |
| Passwordless phone sign-in |
No |
| Phone number and SMS methods |
No |
| Username and password combination |
No |
| Windows Hello for Business |
Yes |
| FIDO2 Security Keys |
Yes |
| Certificate-based authentication |
Yes |
Conditional Access Controls
Conditional Access controls which require device state information, or require specific network location, will provide protection for AiTM.
| Method |
Provides protection for AiTM? |
| Conditional Access Session Controls |
No – simply limits the time window |
| Conditional Access app-enforced restrictions |
No – simply limits downloading/printing data. |
| Conditional Access Continuous Access Evaluation (CAE) |
No – will revoke access in real time once threat response actions are initiated though. |
| Require device to be marked as compliant |
Yes |
| Require device to be marked as Hybrid Entra ID Joined |
Yes |
| Require trusted location (named location) |
Yes |
For many organisations, the simplest approach to mitigate AiTM is to immediately implement device compliance controls. By enforcing device compliance state in Intune as an access control method, you are ensuring that only devices that are enrolled in Intune and align to compliance policies are permitted access. This is the suggested approach for immediate mitigation for organisations that use Entra ID natively.
For organisations that utilise on-premises Active Directory and are not yet in a position to adopt compliance policy controls, we would recommend configuring Hybrid Entra ID Join, and leveraging that as the control.
Lastly, trusted locations can also be applied, however this is less dynamic than device compliance state.