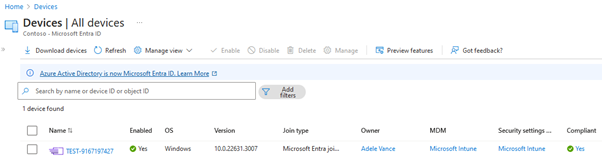
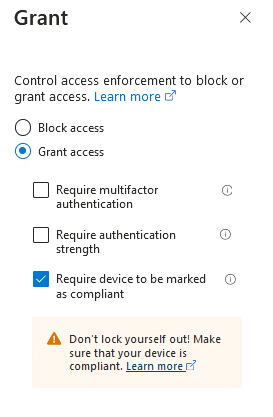
What is device compliance?
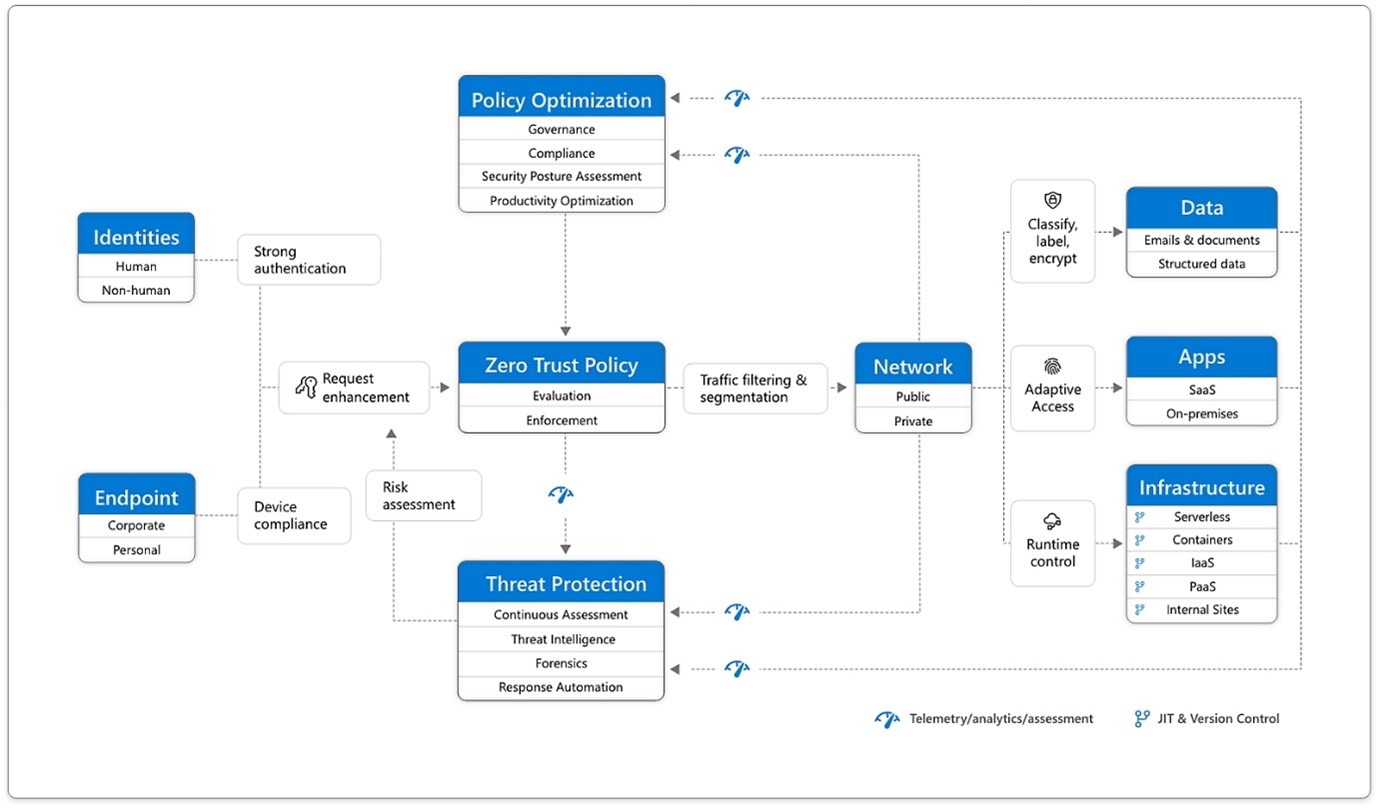
Endpoints are one of the six key elements within a Zero Trust approach. Once an identity is granted access to your resources, data from those resources can flow to the endpoint. However, this can represent a large attack surface—especially if those endpoints aren’t in the state you’d like.
For example, the endpoints may be missing several vendor updates, endpoint protection software might not be installed or might not be running the latest definitions, or the device might not be encrypted.
There may be legitimate reasons for this, e.g. the user has recently returned from annual leave and their device hasn’t been online to receive updates. Regardless of the reason, the state of a device sometimes isn’t compliant with your organisation’s standards and requirements for access to your data.
Microsoft Intune has support for device compliance policies. These policies allow you to configure the requirements for devices to be considered compliant or non-compliant. As an example, you can require that a Windows device has a specific version of Windows, that the device is encrypted or that Defender for Endpoint considers the device to be below a specified risk level; if a device doesn’t meet these requirements, it’s considered non-compliant. You can also create your own custom compliance controls such as requiring that your web content filtering solution is active.
Intune will then evaluate the device against the compliance policy requirements, and mark the device as compliant, or non-compliant. It’s also possible to configure a grace period for any non-compliance, which is useful in the scenario of a newly provisioned device that might not yet meet compliance requirements.
1. Zero Trust Diagram