Passkeys
Research conducted at the time showed that the average person struggled to understand FIDO – it was a complicated acronym that didn’t really explain what it was. To help make it simpler to understand, the term “Passkey” was coined.
When we’re talking about “passkeys”, we’re essentially talking about passwordless FIDO2 credentials.
If you’ve used a FIDO2 security key before, you’ve been using a passkey. To help with wider adoption to the average person, you’ll start to see the term change from “security key” or “FIDO2 security key”, to use the term “passkey” instead.
What does a passkey comprise of?
We won’t perform a technical deep dive in this article, but a passkey comprises a tuple of these three pieces of information:
- User account
- Relying Party – i.e. the system you’re authenticating to with your passkey (e.g. a website)
- Authenticator software – either an app or embedded into the operating system (OS)
You will have a passkey for each provider/website you use, in the same way that you have a username and password currently.
You can simply go to a website, and instead of creating an account with a new password, you’ll be able to select “create a passkey”.
How do passkeys work?
In this section, we’ll provide a high-level explanation of how passkeys are created and how they’re used for authentication.
Passkey creation
Passkeys leverage “public key infrastructure (PKI) cryptography”.
When you create a passkey (let’s assume you’re registering for a website service), your authenticator creates a pair of keys. One is the public key, the other your private key.
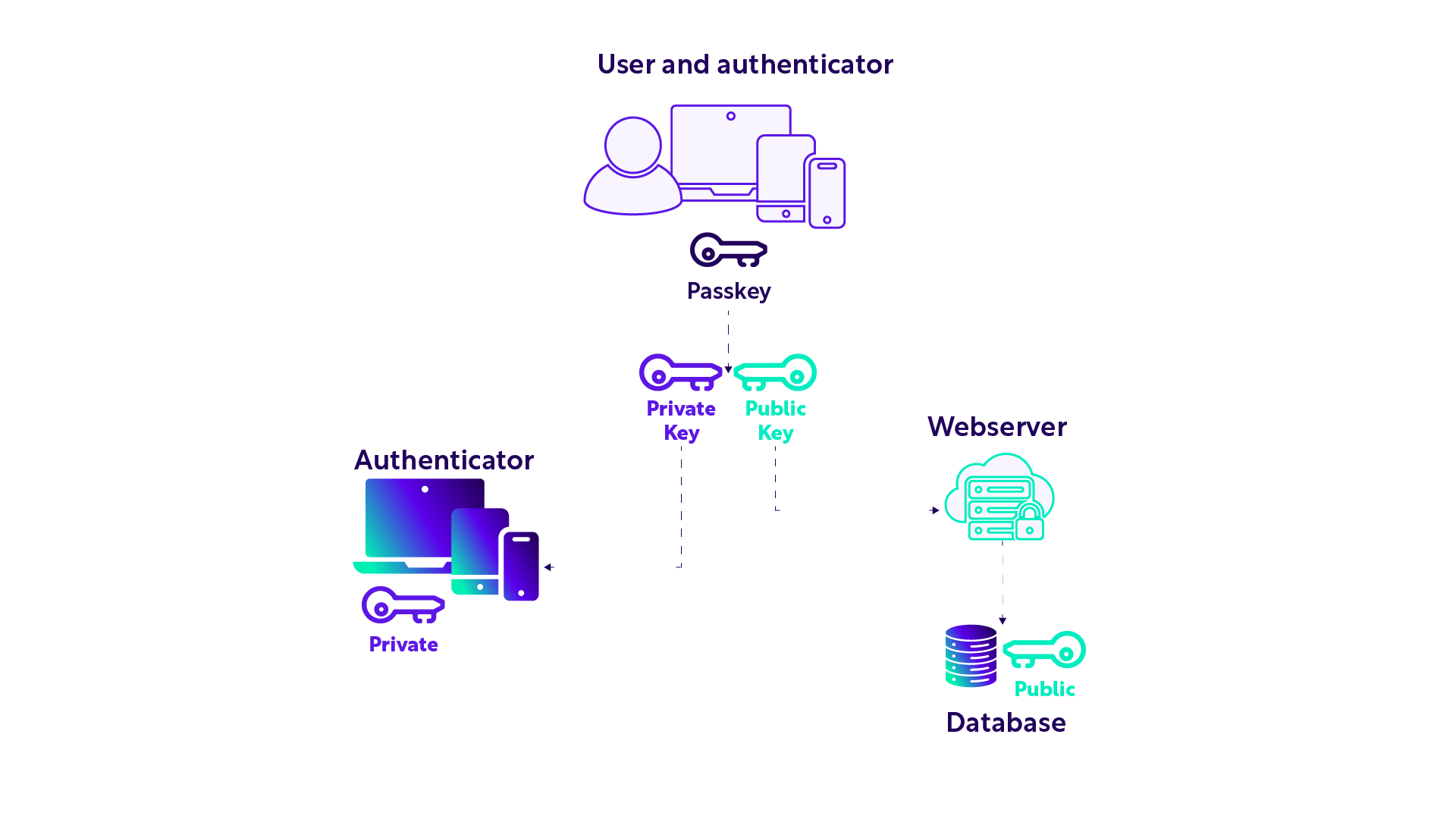
As your keypair is created, your public key is passed to the relying party (e.g. the website provider), where it’s then stored in their database and associated with you as the user. The private key is stored separately on your authenticator.
There isn’t a security issue with sharing your public key, as it’s useless without the corresponding private key.
Passkey authentication (logging in)
So how do you log in with your passkey?
Again, let’s assume a user wants to log into a website with a passkey they’ve already created for that web service.
The graphic below shows how this process works at a high level.
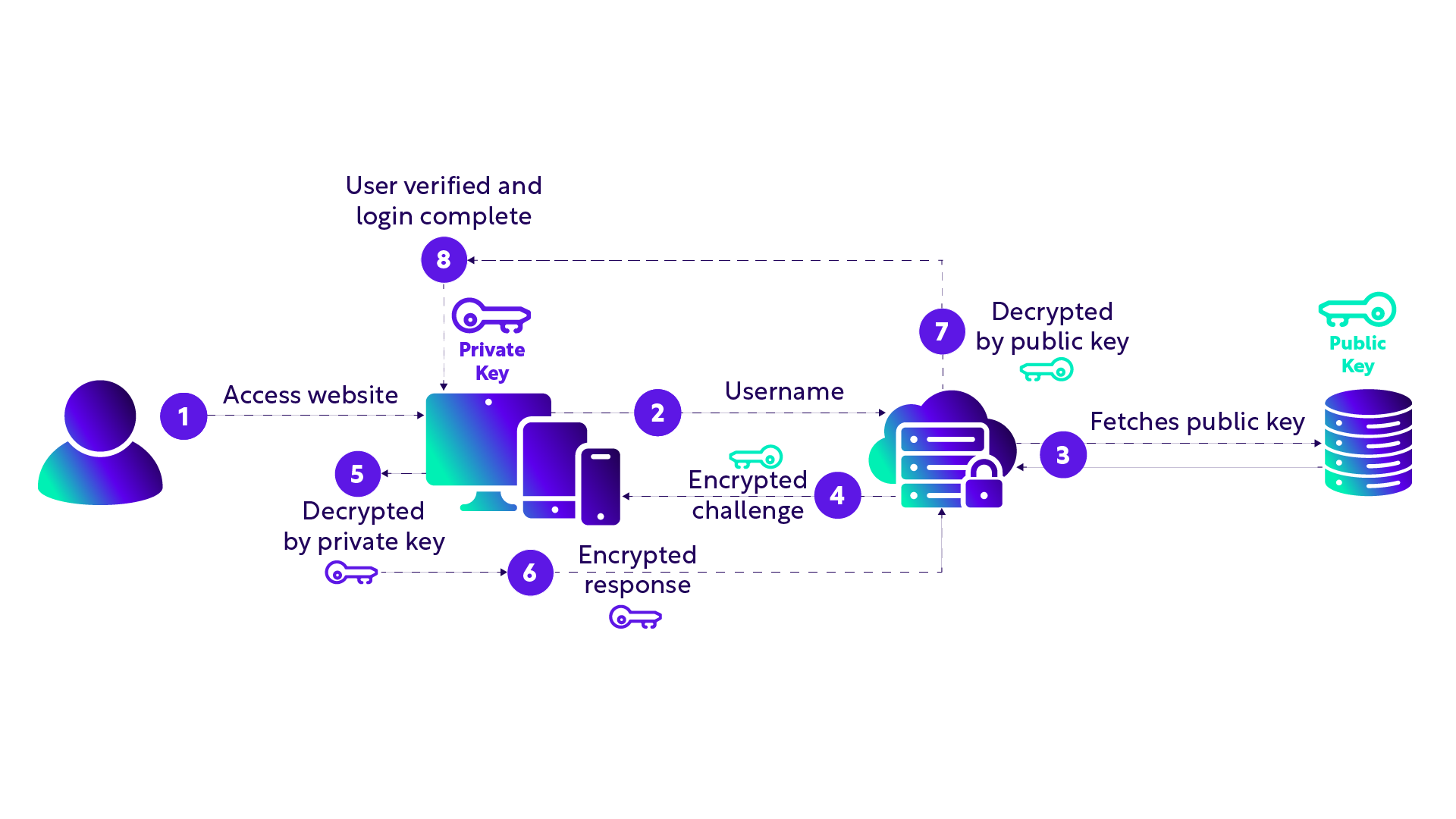
- The user accesses the website’s ‘sign in’ page on their device and browser
- The user chooses the ‘passkey’ sign-in option and enters their username
- The webserver takes the username and checks its database for a public key associated with that username, then retrieves it
- This unique public key is then used to encrypt a ‘challenge’ which is sent back to the user’s device and authenticator
- The user’s private key decrypts the challenge, and the user has to perform some sort of validation action which shows intent (e.g. enter a PIN or biometric)
- The private key is then used to sign and encrypt a response, which is sent back to the web server
- The web server uses the user’s public key to decrypt the response
- This completes the user verification and authenticates the user
Note that no passwords were involved at any point in the process above. This is still a form of MFA, as the authenticator is ‘something you have’ and the biometric or PIN is ‘something you are or know’.
This is also considered phish-resistant, as the authenticator checks for presence/proximity, and intent. Without this, the authenticator cannot release the necessary information. When you sign-in using a passkey, two web standards called WebAuthN and CTAP (Client to Authenticator Protocol) are used to authenticate:
- WebAuthN is used to verify that the website (relying party) matches that of the passkey and other elements. This is partially what makes passkeys phish-resistant. This is because the WebAuthN specification mandates that the URLs match – if an attacker sends you to a phishing website, the URL won’t match that of the URL of the ‘true’ destination, and therefore WebAuthN will reject the authentication attempt.
- CTAP is used as the communication method to validate proximity and presence, and provides cross-device authentication. Therefore, it ensures that when you make an authentication request in a browser, it verifies that you’re physically near your authenticator (for example, by using a Bluetooth connection from the device you’re logging in from to your authenticator on your phone).